1. Prevent Unnecessary Info From Being Displayed
The problem
When you fail to log into a WordPress blog, the CMS displays some info telling you what went wrong. This is good if you’ve forgotten your password, but it might also be good for people who want to hack your blog. So, why not prevent WordPress from displaying error messages on failed log-ins?
The solution
To remove log-in error messages, simply open your theme’s functions.php file, and paste the following code:
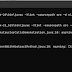
1 | add_filter('login_errors',create_function('$a', "return null;")); |
Save the file, and see for yourself: no more messages are displayed if you fail to log in.
Please note that there are several functions.php files. Be sure to change the one in your wp-content directory.
Code explanation
With this code, we’ve added a simple hook to overwrite the login_errors() function. Because the custom function that we created returns only null, the message displayed will be a blank string.
Source
2. Force SSL Usage
The problem
If you worry about your data being intercepted, then you could definitely use SSL. In case you don’t know what it is, SSL is a cryptographic protocol that secures communications over networks such as the Internet.
Did you know that forcing WordPress to use SSL is possible? Not all hosting services allow you to use SSL, but if you’re hosted on Wp WebHost or HostGator, then SSL is enabled.
The solution
Once you’ve checked that your Web server can handle SSL, simply open your wp-config.php file (located at the root of your WordPress installation), and paste the following:
1 | define('FORCE_SSL_ADMIN', true); |
Save the file, and you’re done!
Code explanation
Nothing hard here. WordPress uses a lot of constants to configure the software. In this case, we have simply defined the FORCE_SSL_ADMIN constant and set its value to true. This results in WordPress using SSL.
Source
3. Use .htaccess To Protect The wp-config File
The problem
As a WordPress user, you probably know how important the wp-config.php file is. This file contains all of the information required to access your precious database: username, password, server name and so on. Protecting the wp-config.php file is critical, so how about exploiting the power of Apache to this end?
The solution
The .htaccess file is located at the root your WordPress installation. After creating a back-up of it (it’s such a critical file that we should always have a safe copy), open it up, and paste the following code:
1 | |
2 | order allow,deny |
3 | deny from all |
4 | |
Code explanation
.htaccess files are powerful and one of the best tools to prevent unwanted access to your files. In this code, we have simply created a rule that prevents any access to the wp-admin.php file, thus ensuring that no evil bots can access it.
Source
4. Blacklist Undesired Users And Bots

The problem
This is as true online as it is in real life: someone who pesters you today will probably pester you again tomorrow. Have you noticed how many spam bots return to your blog 10 times a day to post their annoying comments? The solution to this problem is quite simple: forbid them access to your blog.
The solution
Paste the following code in your .htaccess file, located at the root of your WordPress installation. As I said, always back up the .htaccess file before editing it. Also, don’t forget to change 123.456.789 to the IP address you want to ban.
1 | |
2 | order allow,deny |
3 | allow from all |
4 | deny from 123.456.789 |
5 | |
Code explanation
Apache is powerful and can easily be used to ban undesirable people and bots from your website. With this code, we’re telling Apache that everyone is allowed to visit our blog except the person with the IP address 123.456.789.
To ban more people, simply repeat line 4 of this code on a new line, using another IP address, as shown below:
1 | |
2 | order allow,deny |
3 | allow from all |
4 | deny from 123.456.789 |
5 | deny from 93.121.788 |
6 | deny from 223.956.789 |
7 | deny from 128.456.780 |
8 | |
Source
5. Protect Your WordPress Blog From Script Injections
The problem
Protecting dynamic websites is especially important. Most developers always protect their GET and POST requests, but sometimes this is not enough. We should also protect our blog against script injections and any attempt to modify the PHP GLOBALS and _REQUEST variables.
The solution
The following code blocks script injections and any attempts to modify the PHP GLOBALS and _REQUEST variables. Paste it in your .htaccess file (located in the root of your WordPress installation). Make sure to always back up the .htaccess file before modifying it.
1 | Options +FollowSymLinks |
2 | RewriteEngine On |
3 | RewriteCond %{QUERY_STRING} (\<|%3C).*script.*(\>|%3E) [NC,OR] |
4 | RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR] |
5 | RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2}) |
6 | RewriteRule ^(.*)$ index.php [F,L] |
Code explanation
Using the power of the .htaccess file, we can check requests. What we’ve done here is ch


+18.20.50.png)



